Our software has helped secure

A supply chain security tool you can depend on
We are what you've been looking for
An easy-to-use platform to help secure your products and organization.Continuous Monitoring
Get Notified Immediately
- Unlimited GitHub Repositories
- Documentation Analysis
- Customizable Scan Frequency
- Email Notifications
- Slack Alerts
Accurate Results
Less Noise, More Value
- Vulnerabilities With Security Impact
- No Informational Noise
- Vulnerable Locations
- Remediation Recommendations
- Issue Tracking
Supported Ecosystems
We Secure Dependencies Used In:
- Ruby
- Python
- JavaScript
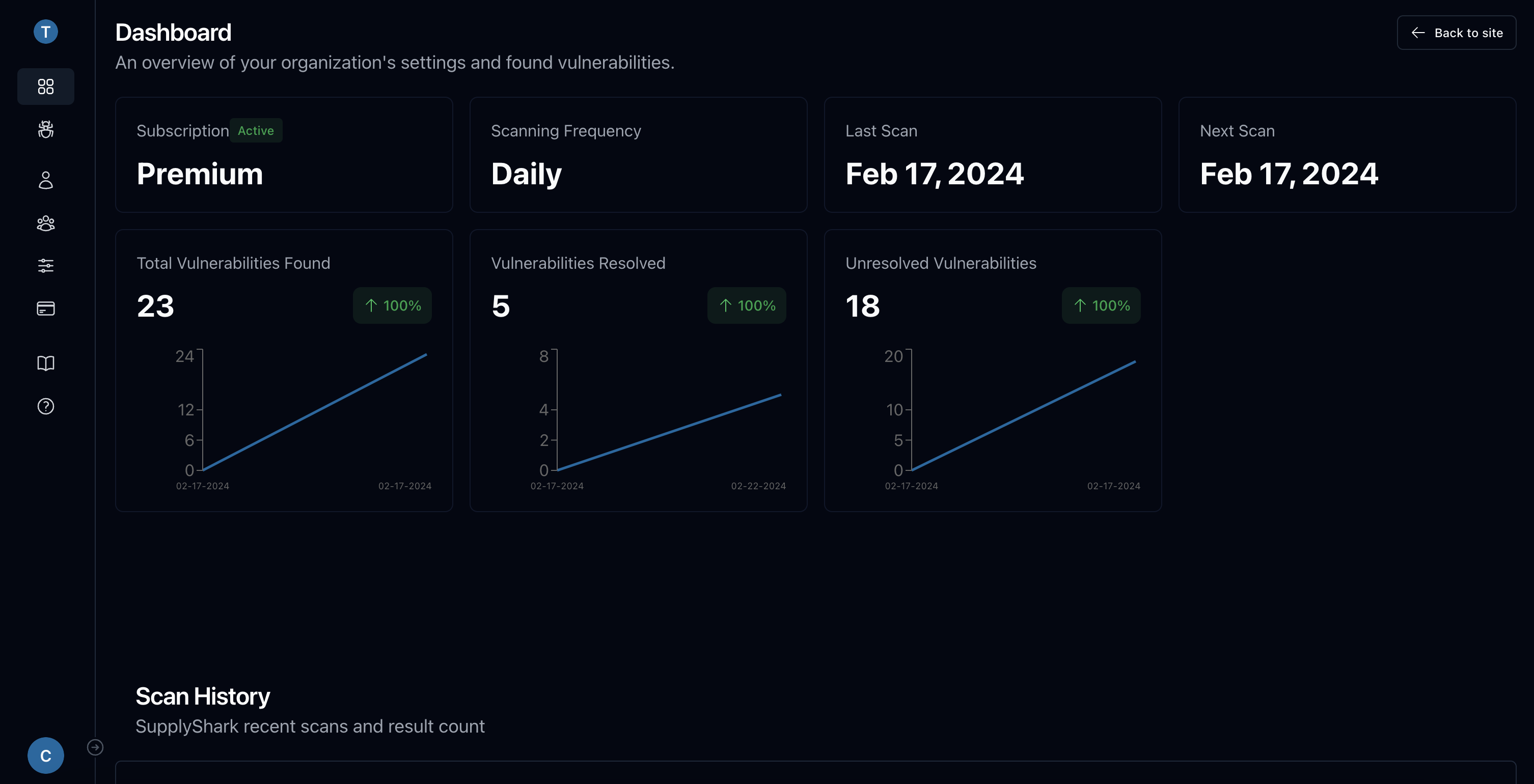
View your progress
Our beautifully designed dashboard contains statistics to help you visualize vulnerability discoveries over time.
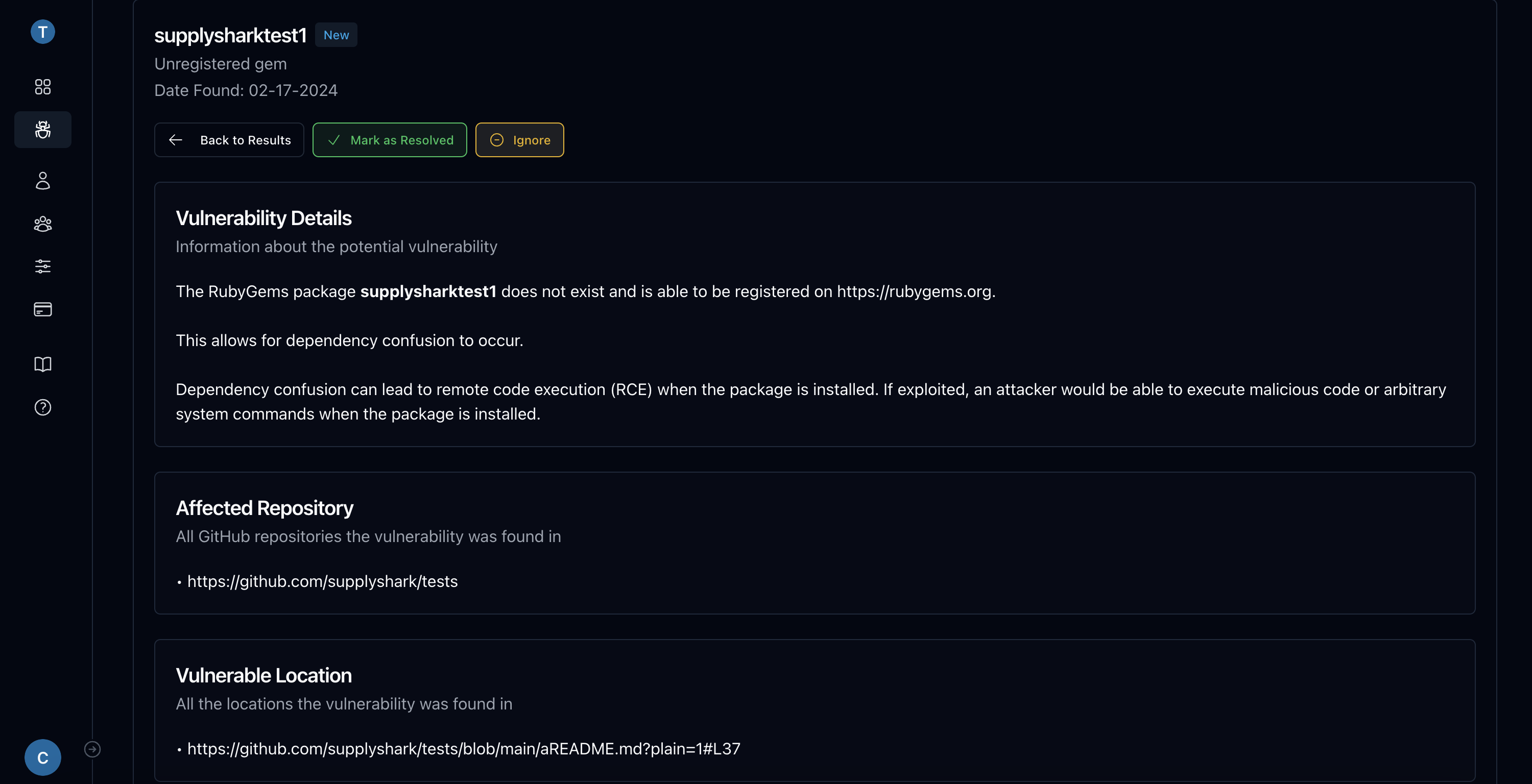
Comprehensive vulnerability reports
Each vulnerability report contains all the information you need to help you understand the issue and fix it promptly.
Get started in just 3 minutes
An easy process
All you have to do is sign-up and install the GitHub app, and we will take care of the rest for you.Sign-Up
Create an account for your organization and invite your team members.
Install the GitHub App
After creating an account, connect SupplyShark to your organization's GitHub by installing the GitHub app.
Choose Your Plan
We have plans perfect for all size businesses.
View Results
Our tool is the best that exists. We will alert you immediately when a potential vulnerability is discovered, but until then you can have peace of mind knowing that you are secure.
Have complete confidence in your supply chain security
What's included
We have everything ready for you to get started.Automated Scans
SupplyShark automatically scans for vulnerabilities in the background and will alert you immediately when a vulnerability is found. You can adjust how often you want SupplyShark to check for issues in the dashboard.
Vulnerability Reports
A vulnerability report is automatically generated for every issue found by SupplyShark. Each vulnerability report includes a description of the issue, every location the vulnerability was found, and remediation recommendations.
Innovative Research
Our research team is constantly looking for new ways hackers can attack your supply chain, and many vulnerabilities we look for are unique methods not publicly known yet. You will be the first to know if you are affected by a new vulnerability technique discovered by our team.
Issue Tracking
In the dashboard, you can track which vulnerabilities are new and need action, which vulnerabilities you've fixed, and which reports you don't want to fix.
Email Notifications
A summary of results found (containing no vulnerability data) will be emailed to the email address you've signed up with. You can customize your email preferences to send these emails to a team email to alert your security team if it helps with your workflow.
Slack Integration
Install our Slack bot to your Slack instance and to receive alerts via Slack every time SupplyShark finds a new issue. Slack alerts will only contain the total amount of vulnerabilities found and a link to the inbox to view the results.
Plans for all size businesses
Which plan is best for your business?
Starter
/Yearly
- Unlimited Public Repositories
- Documentation Analysis
- Weekly Monitoring
- Email Notifications
- Slack Alerts
Pro
Most Popular
/Yearly
- Unlimited Public Repositories
- Documentation Analysis
- Daily monitoring
- Email Notifications
- Slack Alerts
Premium
/Yearly
- Unlimited Public Repositories
- Unlimited Private Repositories
- Forked & Archived Repositories
- Documentation Analysis
- Daily Monitoring
- Email & Slack Alerts
Read about the latest news
Latest Blog Posts
View the latest updates from our team·4 mins reading
A comprehensive guide on hackers can hijack the installation instructions in your documentation leading to remote code execution and malware installation.
·3 mins reading
A real-world example demonstrating how a hijacked npm scope can lead to remote code execution on the developer's computer.
·2 mins reading
A real-world example demonstrating how a hijacked gem package can lead to remote code execution that affects users following installation instructions.